Before you can understand what to do with a cybersecurity MBA degree, it’s important to cover the essential terms in the industry. Cybersecurity is much in demand and it’s no wonder why. News outlets report on high profile data breaches on a weekly basis. These serve as warnings for organizations not to be caught off guard by today’s savvy cybercriminals.
What is the difference between cybersecurity vs information security?
Information security harkens back to the first days that people began to keep secrets from one another. Before cyberspace, files and documents were locked away behind closed doors. Once computers came on the scene, network security was needed to protect electronic assets with vital information. Then, The internet changes the game completely. However, the vast possibilities of this new technology also became a cause for concern. Cybersecurity arose to answer the need for secure transactions and data exchange in cyberspace.
When trying to define information security vs cybersecurity, it’s important to note that both are critical to keeping information an asset secure. However, cybersecurity is the center of discussion in these days of hackers and malefactors breaking into insufficiently protected networks.
Arguably, some analysts believe that information security forms a broader umbrella including the data and information available in electronic form as well as older print media. Cybersecurity then would be a subset of information security that protects connected systems that are vulnerable to cyberattacks on the internet. Network security also plays a role in protecting a company or entity from online threats.
What are some of the key definitions in cybersecurity for executives?
Information security
The SANS Institute defines information security as methodologies implemented to protect electronic, print and other confidential, private information. Information security includes everything from the lock on the file cabinet to multifactor authentication used to protect your login credentials. These measures prevent the use, destruction or disruption of data through unauthorized access. This differs from cybersecurity, which does not include print media, focusing instead on electronic forms of data storage and distribution.
Cybersecurity
When comparing cybersecurity vs information security, the former concentrates on networks, programs and systems vulnerable to digital attack, according to experts at Cisco. Cyberattacks aim to destroy, change and access private or sensitive information for the purpose of interrupting business processes and getting money from organizations that fall victim to data breaches.
Network security
Network security includes both software and hardware solutions to protect your network infrastructure. According to the SANS Institute, network security helps to prevent the following:
- Unauthorized access
- Modification
- Destruction
- Misuse
- Improper disclosure
- Malfunction
This helps IT managers protect their companies from attacks to the IT infrastructure that can cause downtime and compromise customer and company data.
What is the CIA triad in cybersecurity for executives?
The CIA triad is a great way to remember the relationship between network security, cybersecurity and information security. CIA sometimes brings to mind clandestine operations and the exciting world of spycraft. White not so far from the truth, CIA here stands for confidentiality, integrity and availability.
Security experts focus on these elements when they write policies that impact how users interact with the network. The primary goal of cybersecurity professionals is to make users aware of the risks and to help protect their personal data, sensitive company data and private information about customers.
Confidentiality
Confidentiality refers to protecting information by making sure that it is inaccessible to people and devices that are not authorized to access it. This is achieved through physical and digital means. Encryption, IDs and passwords, multifactor authentication and other strategies can thwart hackers and give customers confidence that their personal details are safe within the company”s databases. Without implementing these safeguards, companies leave their data to the mercy of cybercriminals.
Integrity
When data is protected from unauthorized access, people who use the data trust that the data is accurate and protected.
Availability
At the same time that systems keep out unauthorized users, IT managers must ensure that legitimate users have access to highly available data. This requires vigorous monitoring and maintenance of network and other IT assets. Keeping up with security updates and ensuring that backups are done on a regular basis can help guarantee that users will be able to access accurate data when they need it the most.
The CIA acronym can help you understand the difference between information security vs cybersecurity. This baseline standard can help organizations evaluate their existing cybersecurity plan and help implement robust systems that can protect the organization going forward.
What Accreditations Apply to a Cybersecurity MBA?
MBA programs are accredited by one of three organizations:
- Association to Advance Collegiate Schools of Business (AACSB)
- Accreditation Council for Business Schools and Programs (ACBSP)
- International Accreditation Council for Business Education (IACBE)
National Accreditation
A national accreditation organization is a non-regional agency that approves scholastic programs. This practice began in 1912 with a group of vocational schools that created the first accrediting agency. Since then it has grown into a tradition that colleges and universities uphold. In fact, schools without national and regional accreditation are routinely dismissed by licensing boards and hiring companies. These days, national accreditation agencies evaluate vocational, career and trade schools. They particularly focus on schools with career degrees and differ from accreditation boards for traditional liberal arts education schools typically accredited by regional institutions.
Regional agencies also grant accreditation to local higher education institutes. The majority of U.S. colleges have some kind of regional accreditation. At the regional level, the country is divided into six distinct geographic regions. For instance, the Southern Association of Colleges and Schools Commission on Colleges handles universities in the southern states, and central states from West Virginia to Arizona look to the Higher Learning Commission for the stamp of approval.
So, what does regional accreditation or lack thereof mean for universities? Institutions that meet the most rigorous standards regarding academics receive accreditation from their regional organization. These colleges receive more attention from students, donors and other interested parties. Without accreditation, it’s more difficult for schools to receive funding and approval for financial aid for students.
Students who earn credits at accredited colleges and universities are more likely to have their credits transferred to a new school. Some traditional and online MBA programs only accept undergraduate degrees from regionally accredited schools.
There are programmatic accreditation agencies that verify the academic rigor of departments within an institution. This list includes business schools the receive accreditation above and beyond the university’s regional credentials.
In order to earn and keep specialized accreditation, colleges and universities must pass scrutiny on faculty qualifications, student outcomes and other criteria. Programmatic agencies evaluate the standards of specific departments to ensure that they are offering curricula that meet the high standards in that particular field.
Agencies review each program’s curriculum to determine whether they meet standards that include faculty qualifications, student outcomes and other criteria. Programmatic accreditation is conducted by agencies that specialize in particular fields.
When searching for the best online MBA programs with cybersecurity specialties, students should look for accreditation at the business level and recognition by various licensing and certification organizations for cybersecurity and technology. The more prestigious the accreditation, the more valuable the degree or certificate will be.
What Types of Cybersecurity and Information Security MBA Degrees Are There?
The easiest way for students interested in MBA cybersecurity to find out what different universities offer in terms of a cybersecurity MBA is to spend some time searching for accredited schools in their area, or online schools with concentrations that appeal to their interests. Here are a few examples of how schools package cybersecurity MBAs and information security MBA programs. Many cybersecurity MBA and MBA in information security programs can be completed in a year.
- At Fayetteville State University, Students can work toward a convenient online MBA certificate in cybersecurity management. US news and World Report ranks this program #106 among top online MBA programs. FSU has received AACSB accreditation.
- Texas A&M University-Commerce has a College of Business offering several business degrees including an online MBA with a minor in Cyber Security. Also receiving the stamp of approval from AACSB, this program offers various specializations and takes 30-48 credits to complete.
- At the University of Maryville’s Simon School of Business, future cybersecurity professionals can complete an online Cybersecurity MBA accredited by ACBSP. This MBA in cybersecurity ranks among US News and World Report’s best online MBA colleges at #156. The program requires 39 credits and students attending full-time typically finish it within one year.
Other schools offer an MBA in information security. The focus in some programs for information security MBA has a slightly broader scope than an online MBA in cybersecurity degrees that focus on planning and execution of cybersecurity.
An online MBA cybersecurity is a convenient alternative that appeals to students with jobs and families. Whatever track a student chooses in pursuit of an MBA in cybersecurity, accreditation is extremely important to future job prospects. Finding an MBA cybersecurity program with regional and national accreditation is important, especially for those aiming for future roles as leaders in their organizations.
Fortunately, there are a variety of colleges and universities that have an online MBA in cybersecurity with unique programs designed to keep company data and personal information safe. An online MBA cybersecurity degree is something like a badge of honor and grateful employers are willing to pay for these credentials.
What Certifications & Licenses Are Available?
Security+ is a certification granted by CompTIA. many consider it the main cybersecurity certification. You do not need a cybersecurity MBA to sit for this exam, however, it certainly helps. Working towards this certification gives you a foundation in cryptography, vulnerabilities and risk management.
Network+ Certification is also gained through CompTIA. you don’t need this certification for most jobs in the field. However, it provides a great foundation for how networks and computers communicate and helps you master Best practices in cybersecurity.
International Information System Security Certification Consortium, also known as (ISC)². Offers CISSP certification. This can be obtained as part of a graduate certificate in cybersecurity or after obtaining your cybersecurity MBA. To sit for the exam, you must have the following experience:
- Five years of experience in cybersecurity or related industry
- knowledge of two of the eight domains defined by the certification
Obtaining a cybersecurity graduate certificate can help you qualify for the five years of experience. See certification requirements for specific details on how this works. If you already work in architecture, management or engineering, you can focus on furthering your knowledge about your specific specialization.
Another cybersecurity certification is called the Certified Network Defense Architect (CNDA). this certification is for government employees and is governed by the EC-Council. To obtain this credential, candidates must have two years of information technology experience prior to sitting for the exam. Getting your Security+ is a great stepping stone on the way to obtaining the CNDA credential. It teaches you to think like a hacker so that you can defeat them and protect your employer against cyberattacks.
Students who already have an MBA may want to consider a cybersecurity graduate certificate online. There are also in-person programs for a graduate certificate in cybersecurity for learners who prefer that format.
Boston University offers a Certificate in Cybercrime Investigation & Cybersecurity. This cybersecurity graduate certificate teaches students about data breaches, cyberattacks and hacking.
Online graduate certificate programs in cybersecurity can help you advance in your current position or switch to cybersecurity from a related technology or business field. Getting a cybersecurity graduate certificate online shows employers that you care about keeping current and can help you find a new job if you are ready to relocate to an area where these skills are in high demand.
What Are the Best Careers with a Cybersecurity MBA?
Here is a look at some of the jobs for MBA in cybersecurity recipients.
Systems Administrator
Job descriptions for a system administrator may not include a cybersecurity MBA. However, new jobs in cybersecurity that require MBA include employers looking for formal education and a commitment to the field. A systems administrator handles software and hardware for all the computers and devices in a company. This requires knowledge of the latest updates and patches to help keep devices and systems secure.
IT Manager
IT managers oversee IT employees and safeguard IT infrastructure. IT managers minimize downtime and help keep department costs within budget. Upper management depends on IT managers to stay up to date with the latest technology and to inform them of how new solutions can benefit the organization.
Network Administrator
Network administrators troubleshoot issues and fix problems with the company’s network. This role involves installing new systems and maintaining speed and security standards.
Cybersecurity Analyst
Key MBA information security jobs include roles as cybersecurity analysts. These employees protect the company’s data and network. Cybersecurity analysts respond to breaches and take steps to protect company hardware including desktops and other employee devices.
Security Engineer
Security engineers design and implement information security strategies and then maintain these solutions. They document the security posture of an organization and suggest any measures that can improve the company’s cybersecurity.
Security Consultant
Security consultant roles are some of the most lucrative jobs for MBA in cybersecurity graduates. These cybersecurity professionals evaluate the company’s security status and act as advisers to IT professionals. These consultants help companies raise their threat management level by planning, testing and managing the most effective security protocols.
Information Security Analyst
The information security analyst is responsible for protecting the company network and maintaining all defences against an attack. The analyst may also implement the company’s disaster recovery plan in the event of network outages.
Information Security Manager
MBA information security management jobs include information security managers. These professionals develop the procedures and policies that keep the company network secure. They manage security analyst and make sure that the organization complies with standards and norms. This includes state and federal regulations as well as industry compliance standards.
Chief Information Security Officer (CISO)
MBA information security jobs Can lead to top management positions such as the CISO. This executive position overseas a company security strategy. This includes security breaches and compliance with industry and legal rules, regulations and standards.
New jobs in cybersecurity that require MBA degrees include more and more roles like those above. Data breaches and threats from hackers created some new roles, such as the CISO. MBA information security management jobs are likely to continue to grow as demand increases.
What Salary Can I Make With a Cybersecurity MBA?
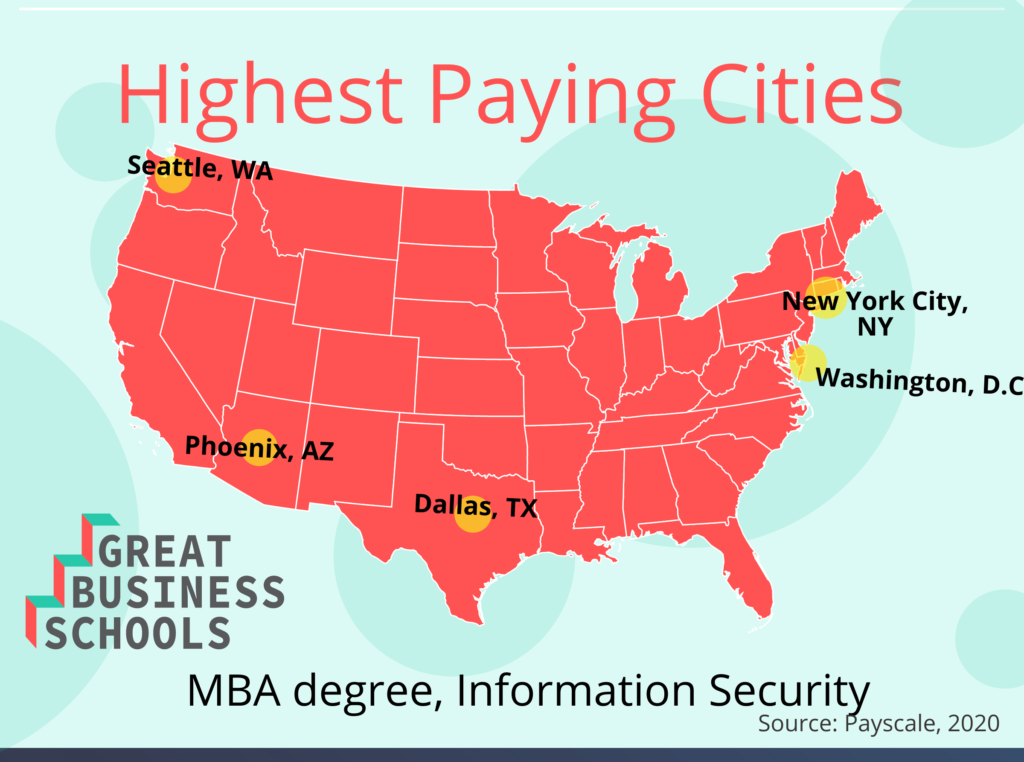
Once students obtain their MBA in cybersecurity, they can find work at one of the fastest-growing fields. These highly valued resources have their pick of companies in industries to work for. Salary, as with any other industry, is commensurate with experience and depends on the location of the company as well as other factors.
According to Payscale, cybersecurity jobs for those with advanced degrees average $98,000 per year.
- IT Business Analyst $88k
- Fraud Investigator $86k
- Cyber Security Analyst $98k
- Information Security Manager $127k
- IT Director $105k
- Project Manager $102k
Some of the companies that pay a great cybersecurity masters salary include:
- Northrop Grumman Corporation $64k
- Booz, Allen, and Hamilton $90k
- Microsoft Corp $110k
- Synergy Global Solutions $101k
- Citigroup, Inc. $106k
Getting your degree can result in higher MBA information security management salary opportunities. Many cybersecurity masters salary expectations fall close to or above six figures. If you have industry experience, you can command an even higher MBA information security management salary.
Are There Any Professional Organizations Pertaining to Cybersecurity?
Here are some of the main organizations for cybersecurity professionals. Professional organizations offer networking opportunities as well as the ability to continue your education and remain relevant in the job market.
The International Information Systems Security Certification Consortium, Plays an important role in educating and certifying cybersecurity professionals.
ISACA is a worldwide organization concentrating on governance and security. This organization sets standards for professionals and offers industry certifications. Members attend conferences and contribute to industry publications.
The AITP is also a worldwide society for IT professionals. It holds conferences and webinars and provides awards for students and professionals in the field. AITP manages a useful job board and has over 4,500 members.
The Information Technology Infrastructure Library (ITIL) has developed paradigms for IT development, infrastructure an operations.
Forum of Incident Response and Security Teams
FIRST Provides a way for response teams to share experiences and tips. The organization sponsors meetings and conferences and offers web repository’s where members can share their information with other professionals. This practical forum is it gold mine for those new to the field or wishing to contribute to the industry.
This institute is the most trusted source when it comes to information security training. SANS certifications and courses incorporate many security niches. Founded in 1989, SANS has educated thousands of professionals. it began humbly as a research organization but has evolved into an educational resource for security professionals. The site includes papers, webcasts and blogs as well as newsletters for the edification of members.
ISSA (Information Systems Security Association)
ISSA is a nonprofit association. It aims to provide networking opportunities as well as growth opportunities for cybersecurity professionals. It has a global reach and host conferences as well as local chapters.
CIS (Center for Internet Security)
CIS caters to corporate entities in the private and public sectors. It is not designed to meet the needs of individuals per se. It delivers robust training solutions to enhance workforce development. CIS compiles case studies and offers products and services at a deep discount or for free.
These are just some of the many industry organizations that professionals can join to network, improve their skills, and show involvement. explore these top organizations or find ones that cater to your interest and professional goals.
Becoming a cybersecurity MBA takes a bit of sacrifice. However, most programs can be completed in a year and are offered online. These degrees open up doors due to the scarcity of qualified individuals for these positions.
Carrie Morris
Author
Warren Dahl
Editor-in-Chief
Ready to find the perfect business program?

